In a layman’s view, Quantum Entanglement may refer to a scenario where we may have incomplete knowledge of the state of two similar states¹. Our classic computation technology uses a “definite bit system” of 0s and 1s to process human input. However, with increasing problem bases like efficient cybersecurity and expanding the Internet of Things (IoT), current classical supercomputers are experiencing difficulties in keeping up with effective solution-seeking.
Why understand quantum entanglement?
Understanding quantum computing promises the improvisation of computation capabilities, boosting complex problem-solving capacities that are rapidly increasing. According to Ryan Gordon at IBM, quantum computing refers to the process of leveraging certain quantum physics principles to solve problems too complicated for classical computers, using “qubits” to execute multidimensional algorithms². Researchers at the University of Waterloo defined a qubit as an “advanced bit” that can exist in a superposition state and even exemplify entanglement with one another³. Furthermore, they affirm that the possibility to extract the potencies of superposition, entanglement, and interference makes qubits possess much more power than classical bits.
1. Spin Qubit in Quantum Cryptograph

Figure 1: The Rydberg (left), spin (centre) and orbital (right) degrees of freedom have qualified as base states for quantum computing with the spin qubit having promising implementation (Wikimedia Commons: Prixz5nu).
According to research posted by Yu and colleagues, quantum particles imitate small magnets— this can be inferred as a property— where spin direction can either be up or down but not in the middle⁴. As the IoT increases, there is a need for privacy since end-to-end consumers share data. The integrity of this medium can be improved through quantum computing. According to Gustavus Simmons, current encryption relies on Rivest-Shamir-Adleman encryption, popularly known as RSA, in which a user chooses a secret key (that he or she can choose to share) using prime numbers so that their factoring effectively eliminates the possibility of a compromise using our computing cypher decryption capability⁵.
In as much as the method seems secure, many companies have implemented it insecurely leading to leakages of secret keys thus compromising user data⁶. Quantum cryptography relies on quantum key distribution instead of the RSA key exchange mechanism. This works where components of data are encrypted using qubit spins. Relying on the spin states, a simple spin qubit can be built for cryptographic tasks where if a sender sends a message, the end-receiver has to expect the message to arrive in a state known to them pre-hand.
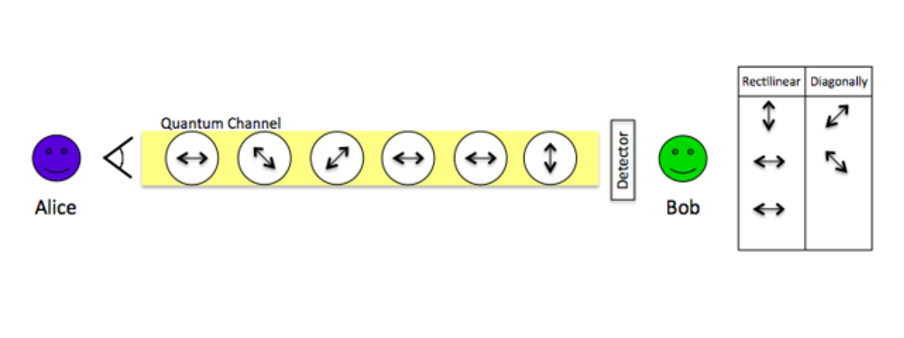
Figure 2: To depict how quantum cryptography works, the random basis and qubit order are chosen by Alice. She then uses the quantum channel to deliver to Bob the qubits as photons. When Bob finds these qubits, he logs his findings in a table. Bob has a hunch about Alice’s reasoning based on the table and can decipher the intended message (Wikimedia Commons: Cku04).
Research published by Haw and colleagues finds that a significant advantage is that the states cannot be known using classical communication but only quantum technology⁷. The article further clarifies that copying data encoded in a quantum state is impossible through the no-cloning theorem or wave function collapse: if attempts by eavesdropper surface to read the data, the conditions of the qubits will be disturbed, thus changing states that can signal to the receiver/sender that the data is being manipulated in transmission.
2. Superconducting Qubits in Computing Architecture
According to Google TensorFlow, classical computers require much more energy to keep the physical bits, which are in the form of electrons, in the Dynamic RAM⁸. This is because the electrons are light and noisy; thus, external disturbances like magnetism and movement through classical processor architecture disturb them, leading to electron leaks out of the Dynamic RAM (DRAM). The DRAM thus constantly needs the power to reinforce excess bits in case of losses every single time.
Ryan Mandelbaum at IBM reports that the process of reinforcing bits requires much more energy; quantum computers rely on cold processors that create superconducting qubits immersed in supercooled fluids⁹. He further explains that in these low temperatures, a quantum mechanical effect is exhibited by some processor materials allowing electrons to actually move through them without resistance leading to stable states making them “superconductors”. When more electrons traverse through the superconductors, they match creating some pairs that easily carry charges through quantum tunneling. Two superconductors are then placed on either side of an insulator creating the Josephson junction. The Josephson junction is a junction onto which photons are fired where a hold of their characteristics regarding the amount/content of quantum information carried by them is extracted creating the superconductor bits¹⁰.
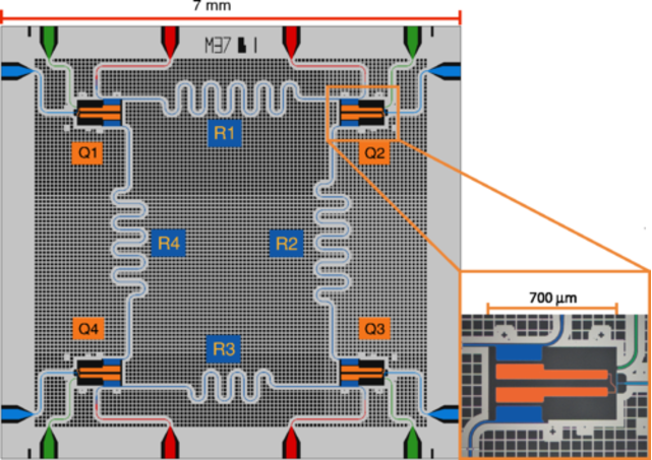
Figure 3: High-level depiction of superconducting qubits Q1-Q4 and their arrangement on a processor (Wikimedia Commons: Y.salathe et al.).
3. Photon qubits in sensory devices
Manoukian proposes that the polarization of photons— where each photon holds an electromagnetic field with a certain direction of polarity— can be used to enhance the sensitivity of some of the crucial sensory devices by creating “photon qubits”¹¹. The common two states used to specify the qubit position are horizontal and vertical. LCDs use polarization filters to block excess light depending on how polarized they are if light emission increases beyond the requirement. Tse and colleagues are investigating how photon-based qubits are enhancing the sensitivity of the Laser Interferometer Gravitational-wave Observatory to exhibit minuscule light disturbance leading to accurate Wave detection¹².

Figure 4: A demonstration showcasing the photon qubit scenario where if we employ a horizontal polarization test to the two photons A and B released from the same source S, one photon will certainly fail while the other will undoubtedly pass, enhancing the sensitivity of the device (Wikimedia Commons: Mliu 92).
Meanwhile, Angelica Sanchez reports that researchers at the Reimer Lab in Waterloo, Canada are creating medical imagery and detection sensors that could help in cancer treatment where she notes that classical sensors, in this case, have a limitation: they cannot detect small tumours¹³. This leads to most classical sensors reflecting most of the light when aimed at them. Therefore, the researchers are implementing a quantum sensor that can detect every single photon from UV to Infrared. By capturing every photon, they rely on time qubits that refresh for the next one within a second. They then create an array of tampered nanowires that convert the coming photos into a current that can be exponentially increased and recognized in a superior manner¹³.
Another breakthrough is at Kyoto University where an ultra-sensitive sensor that relies on diamond impurities is being researched on. Herbschleb and colleagues report that the nitrogen atom has a higher tendency to get into carbon-based diamonds, resulting in a defect¹⁴. This defect possesses electrons that can ingest green light and produce red photons in the vicinity of a weak magnetic field. Scientists at the Reimer lab are also working to use the detection of the spin of the hydrogen nucleus in the proton to develop extremely sensitive sensors that can construct 3-D images of complex molecules like those of proteins¹³.
References
1. Wilczek, F. (2016, April 28). Entanglement Made Simple. Retrieved from Quanta Magazine website: https://www.quantamagazine.org/entanglement-made-simple-20160428/
2. Gordon, R. Quantum computing with superconducting circuits for MRS Fall Meeting 2020: IBM Research. IBM Research Publications (2020). Available at: https://research.ibm.com/publications/quantum-computing-with-superconducting-circuits.
3. The University of Waterloo. (2021, March 11). What is a qubit? Retrieved from Institute for Quantum Computing website https://uwaterloo.ca/institute-for-quantum-computing/quantum-101/quantum-information-science-and-technology/what-qubit
4. Yu, Q., Dong, D., Wang, Y., & Petersen, I. R. (2020). Capability comparison of quantum sensors of single or two qubits for a spin chain system. IFAC-PapersOnLine, 53(2), 263–268. https://doi.org/10.1016/j.ifacol.2020.12.133
5. Simmons, G. (2020). RSA encryption | Britannica. In Encyclopædia Britannica. Retrieved from https://www.britannica.com/topic/RSA-encryption
6. Crane, C. (2020, January 15). How Secure is RSA in an Increasingly Connected World? Retrieved from Hashed Out by The SSL StoreTM website: https://www.thesslstore.com/blog/how-secure-is-rsa-in-an-increasingly-connected-world/
7. Haw, J. Y., Zhao, J., Dias, J., Assad, S. M., Bradshaw, M., Blandino, R., Symul, T., Ralph, T. C., & Lam, P. K. (2016). Surpassing the no-cloning limit with a heralded hybrid linear amplifier for coherent states. Nature Communications, 7(1), 13222. https://doi.org/10.1038/ncomms13222
8. TensorFlow (n.d.). TensorFlow Quantum. Retrieved from TensorFlow website: https://www.tensorflow.org/quantum
9. Mandelbaum, R. (2021, February 9). New IBM, UC Berkeley paper shows path toward useful quantum. IBM Research Blog. https://research.ibm.com/blog/utility-toward-useful-quantum
10. Kockum, A. F., & Nori, F. (2019). Quantum Bits with Josephson Junctions. Fundamentals and Frontiers of the Josephson Effect, 703–741. https://doi.org/10.1007/978-3-030-20726-7_17
11. Manoukian, E.B. (1996). Quantum field theory of polarization of light by a polarizer. International Journal of Theoretical Physics, 35(8), 1735–1744. https://doi.org/10.1007/BF02302267
12. Tse, M., Yu, H., Kijbunchoo, N., Fernandez-Galiana, A., Dupej, P., Barsotti, L., … McRae, T. (2019). Quantum-Enhanced Advanced LIGO Detectors in the Era of Gravitational-Wave Astronomy. Physical Review Letters, 123(23). https://doi.org/10.1103/physrevlett.123.231107
13. Sanchez, A. (2023, March 29). Using quantum technologies to make precise early-stage diagnosis. TQT. https://tqt.uwaterloo.ca/media-details/using-quantum-technologies-to-make-precise-early-stage-diagnosis/
14. Herbschleb, E. D., Kato, H., Maruyama, Y., Danjo, T., Makino, T., Yamasaki, S., Ohki, I., Hayashi, K., Morishita, H., Fujiwara, M., & Mizuochi, N. (2019). Ultra-long coherence times amongst room-temperature solid-state spins. Nature Communications, 10(1). https://doi.org/10.1038/s41467-019-11776-8
Related Posts
Caribbean History through Genetics and Archaeology
Figure 1: A map of the Caribbean Islands from 1894...
Read MoreTo safeguard Africa’s topmost predators
From Nepal’s bengal tiger to Kenya’s big Lions, conservation of...
Read MoreBeyond the White Coat Worker: An Overview of Citizen Science
By: Olivia Brado1, Luz Mariana Cumpa Gomez1, Shirin Dadina1, Katrina...
Read MoreMind Missing Out? Fear of Missing Out and the Brain
Figure: A person scrolling through news articles on their smartphone....
Read MoreStrength in Numbers: How Community Enhances Perceived Support
Figure 1: Bandmates join in a group hug. The powerful...
Read MoreCOVID-19 Clinical Trials and Racial Disproportionality
Figure 1: A doctor drawing blood from a patient as...
Read MoreFrankline Misango Oyolo